The “Nearest Neighbor” Attack: When Proximity Becomes a Cybersecurity Threat

In the world of cyber espionage, attackers are constantly innovating new ways to breach networks. One of the most fascinating—and chilling—methods employed recently involves exploiting physical proximity to infiltrate targets. This strategy, known as the “Nearest Neighbor” attack, demonstrates just how resourceful and determined threat actors can be. What Is a Nearest Neighbor Attack? A […]
Why Cybersecurity Demands Attention at Every Level of Leadership

Cybersecurity doesn’t fit neatly into traditional business priorities like increasing revenue or cutting costs, and that’s exactly why it often gets overlooked. Yet the reality is stark: failing to address cybersecurity as a strategic risk can halt operations, erode customer trust, and even expose organisations to direct liability. For board directors, this means recognising that […]
Case Study: Unauthorised Access to Hospital Network

In early 2024, a hospital discovered unauthorised access to its network via its managed service provider (MSP). The incident highlighted vulnerabilities in how the hospital managed user access and device security. While no patient care or data was affected, the event revealed critical lessons for improving cybersecurity frameworks. What Happened? How Access Was Gained A […]
ASIC’s Warning to Directors: Cybersecurity is Now a Board-Level Responsibility

As cyberattacks continue to surge in Australia, ASIC has ramped up its scrutiny of corporate boards and directors, holding them accountable for cyber resilience. Directors must ensure that their companies have robust cybersecurity measures, business continuity plans, and response protocols in place. According to ASIC, paying lip service to cyber defence is no longer enough; […]
Why Board Level Cybersecurity Event Simulations are Crucial

Cyber threats have evolved into a critical concern for businesses worldwide, board-level cybersecurity event simulations have become a crucial component of organisational risk management strategies. However, many boards struggle to stay ahead due to a lack of hands-on experience and understanding. Board-level cybersecurity event simulations offer an invaluable opportunity for directors to navigate potential crises […]
Scary new Phishing trick

Phishing attacks are evolving faster than ever, and cybercriminals are now leveraging SVG (Scalable Vector Graphics) attachments to slip past email filters. This new technique isn’t just clever—it’s dangerous. Here’s what you need to know to protect your organisation from falling victim. Why SVG Attachments Are the New Phishing Frontier SVG files are commonly used […]
Privacy or Protection? Balancing the Use of Facial Recognition in Public Spaces

The recent OAIC ruling against Bunnings for its use of facial recognition technology has reignited a critical debate: how can businesses balance the need for physical safety with the obligation to protect customer privacy? The Privacy Problem Facial recognition captures and stores unique biometric data—your face, essentially becoming a digital fingerprint. While the technology offers […]
Benefits of Phishing Simulations for Organisations

As cyber threats grow more sophisticated, organisations must remain vigilant to safeguard their sensitive data and resources. One of the most effective ways to mitigate the risk of cyberattacks is through phishing simulations. Here, we’ll explore the top benefits of phishing simulations and why they should be a cornerstone of every organisation’s cybersecurity strategy. What […]
Why Every Australian Business Needs a Cyber Governance Platform to Stay Resilient
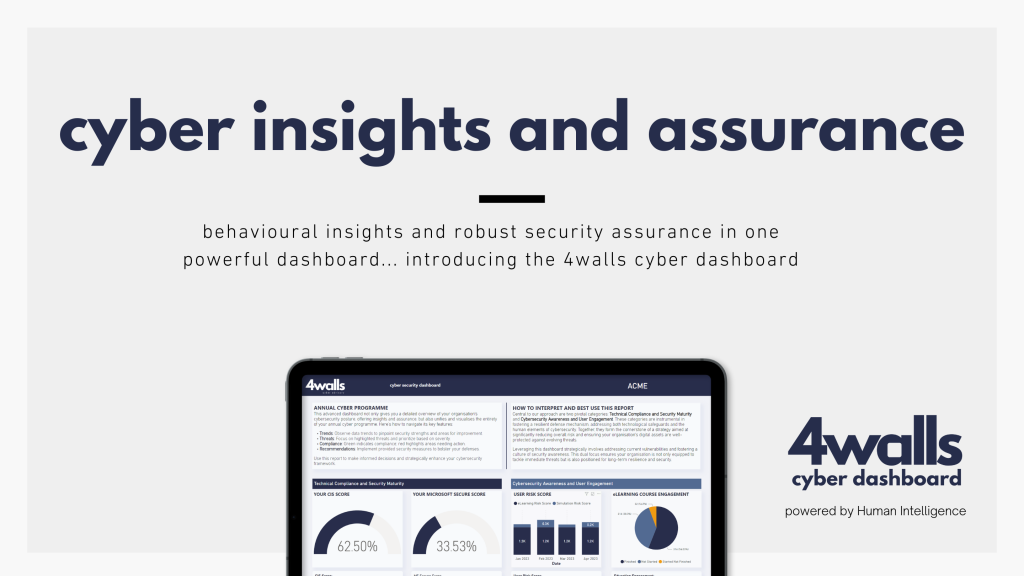
With the rising tide of cyber threats and regulatory pressures, Australian businesses are recognising the importance of a comprehensive cyber governance platform to protect their data, reputation, and operations. A robust cyber governance platform is more than a security add-on; it’s a strategic foundation that ensures organisations can anticipate, detect, and respond to threats while […]
What Australia’s Financial and Telco Sectors Can Learn from Singapore’s Phishing Legislation

As cyber threats grow in scale and complexity, Australia’s regulatory landscape is shifting to ensure that companies take greater responsibility for protecting customers. Singapore has recently introduced a groundbreaking move in this direction: financial institutions and telcos are now mandated to share responsibility for phishing scams. This development has implications for Australia’s own approach to […]
