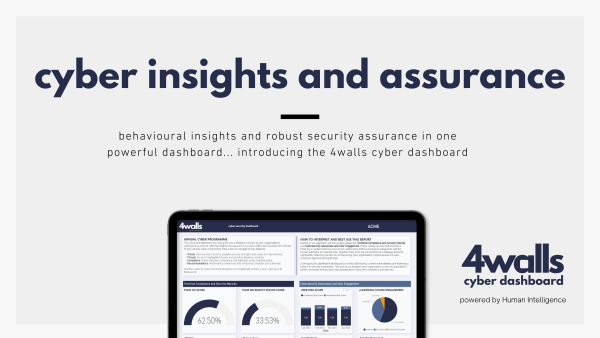
In 2024 cybersecurity is no longer just an IT issue—it’s a crucial part of running any business. With cyber threats becoming more complex and frequent, regular cybersecurity assessments are essential.
This guide walks you through five simple steps to evaluate your cybersecurity measures, protect your business, and strengthen your security posture. Let’s dive in.

Why Cybersecurity Assessments Matter
Understanding the importance of cybersecurity assessments is key. As the digital world grows more complex, so do the risks. Regular assessments help spot weaknesses and improve your defences before attacks happen. It’s an ongoing process, not a one-off event.
Why Are Cybersecurity Assessments Essential?
- Understand Your Security Posture: Know how prepared you are against cyber threats.
- Meet Regulatory Requirements: Many standards like GDPR and HIPAA require regular security checks.
- Stay Ahead of Threats: Regular assessments help you anticipate and prevent attacks.
- Secure Cyber Insurance: Some insurers require regular assessments to provide coverage.
The Cybersecurity Assessment Process
Assessing your cybersecurity involves several key steps:
- Scoping: Define what’s included in the assessment.
- Information Gathering: Collect data about your systems.
- Vulnerability Assessment: Find potential weaknesses.
- Risk Assessment: Prioritise vulnerabilities by impact.
- Reporting: Document findings and recommendations.
Five Essential Steps for Effective Cybersecurity Assessments
- Identify and Assess Risks
- Understand Threats: Know the risks specific to your industry.
- Inventory Assets: List all hardware, software, and data.
- Classify Data: Prioritise data based on sensitivity and importance.
- Establish a Security Policy
- Access Controls: Define who can access what.
- Data Protection: Set rules for data encryption and storage.
- Incident Response: Have a plan for security breaches.
- Implement Security Controls
- Firewalls: Control network traffic.
- Endpoint Protection: Use antivirus solutions.
- Patch Management: Regularly update software.
- Monitor and Evaluate
- Log Monitoring: Check logs for suspicious activity.
- Penetration Testing: Simulate attacks to find weaknesses.
- Incident Response: Monitor and respond to incidents.
- Update and Improve
- Threat Intelligence: Stay updated on new threats.
- Security Awareness: Train employees on security.
- Regular Audits: Conduct routine checks.
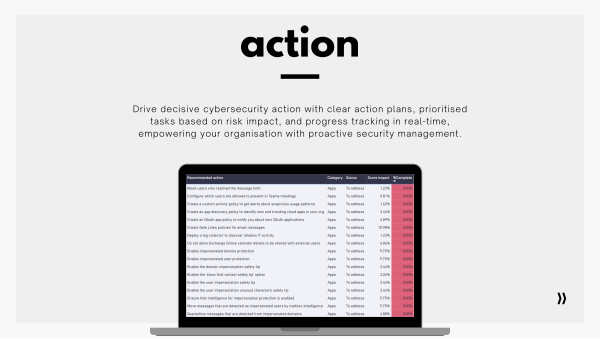
Common Challenges and Solutions
- Limited Resources: Use automated tools to save time.
- Changing Threats: Stay informed about new threats.
- Complex Infrastructure: Consult experts for detailed insights.
Tools and Resources for effective cyber security assessments
- Vulnerability Scanners: Use tools like Nessus for automated checks.
- Frameworks: Follow standards like NIST for structure.
- Consultants: Get expert help for in-depth assessments.
Conclusion: Your Roadmap to Stronger Cybersecurity
By following these steps, you’ll be on track to safeguard your organisation’s digital assets. Regular cybersecurity assessments are crucial for maintaining a secure business environment.
Need help getting started? Contact us today to schedule a cybersecurity assessment.
